CTF练习Week2
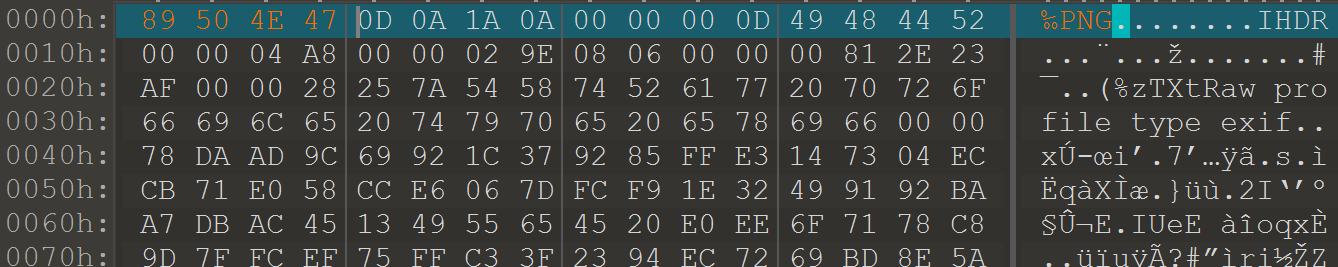
0x00 [UTCTF2020]file header
修改文件头,得到flag
0x01 [GKCTF 2021]excel 骚操作
点击发现,有的空白格上的数值是1。
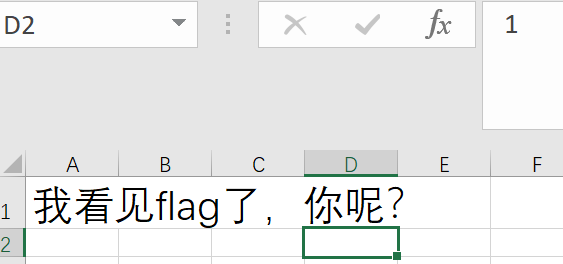
设置单元格式,显示出所有的1
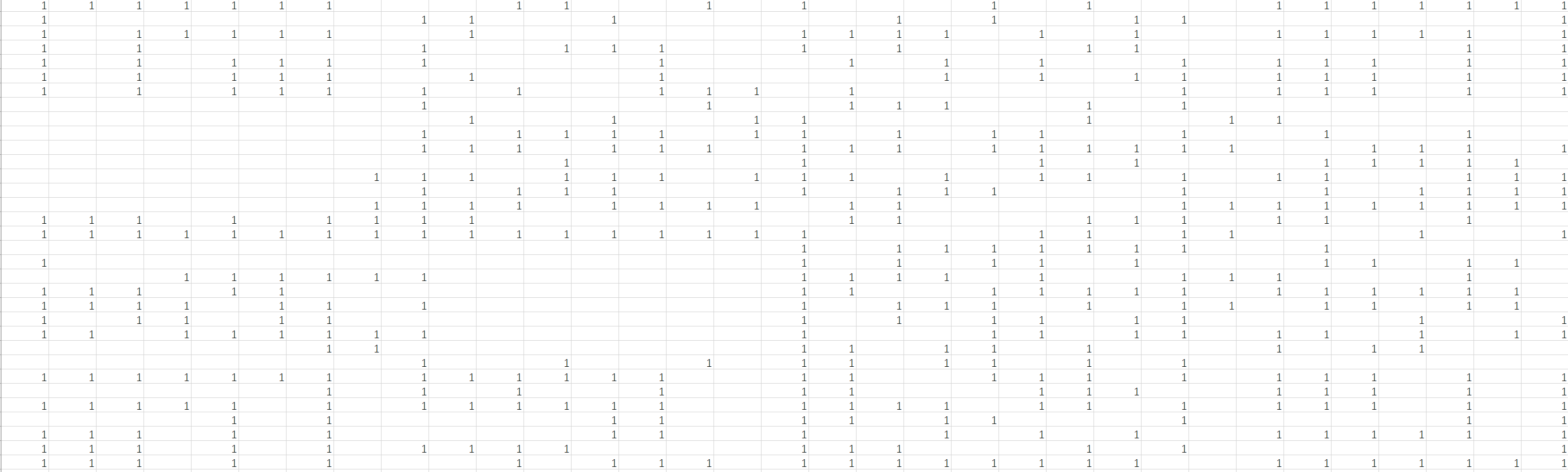
然后设置突出显示,得到汉信码,扫描得到flag。

0x02 [湖南省赛2019]Findme
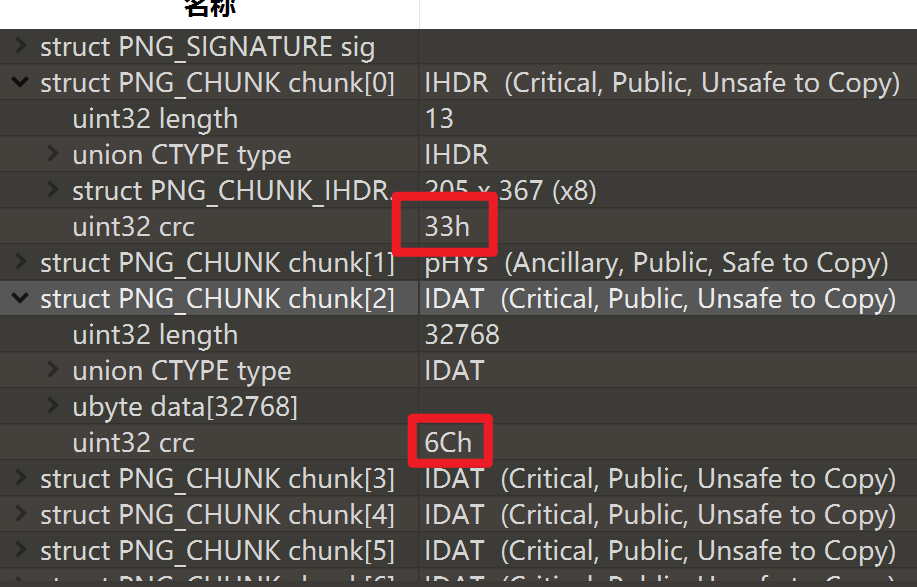
tweakpng分析1.png发现chunk处存在问题
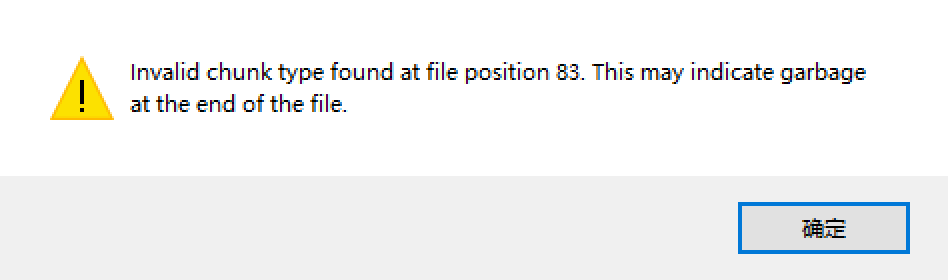
用010分析发现缺少IDAT的标识,手动添加一下。
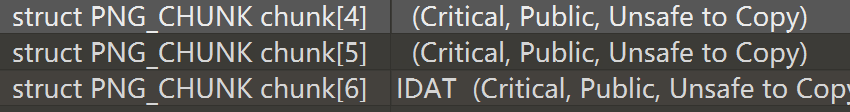
脚本爆破宽高
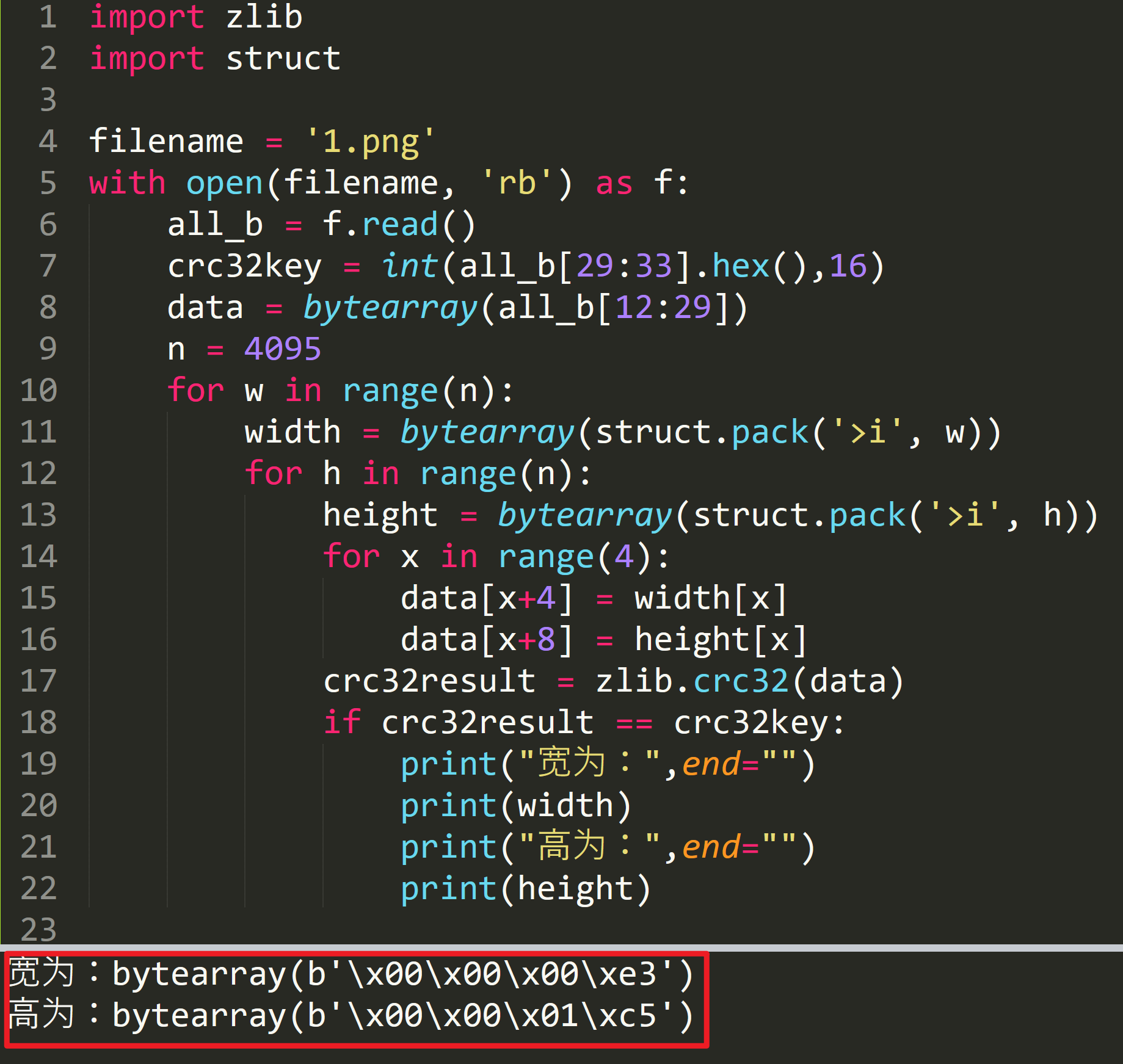
import zlib
import struct
filename = '1.png'
with open(filename, 'rb') as f:
all_b = f.read()
crc32key = int(all_b[29:33].hex(),16)
data = bytearray(all_b[12:29])
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = zlib.crc32(data)
if crc32result == crc32key:
print("宽为:",end="")
print(width)
print("高为:",end="")
print(height)得到

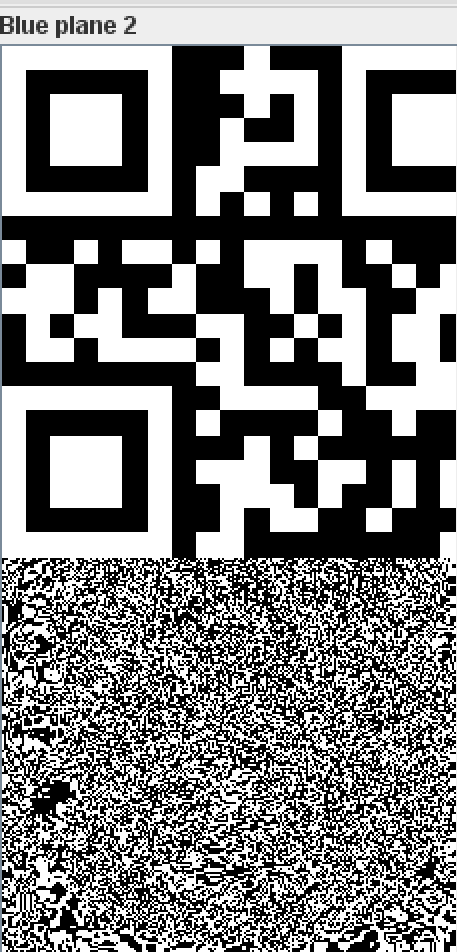
放到stegslover里面,在bule2时发现二维码,扫描得到ZmxhZ3s0X3
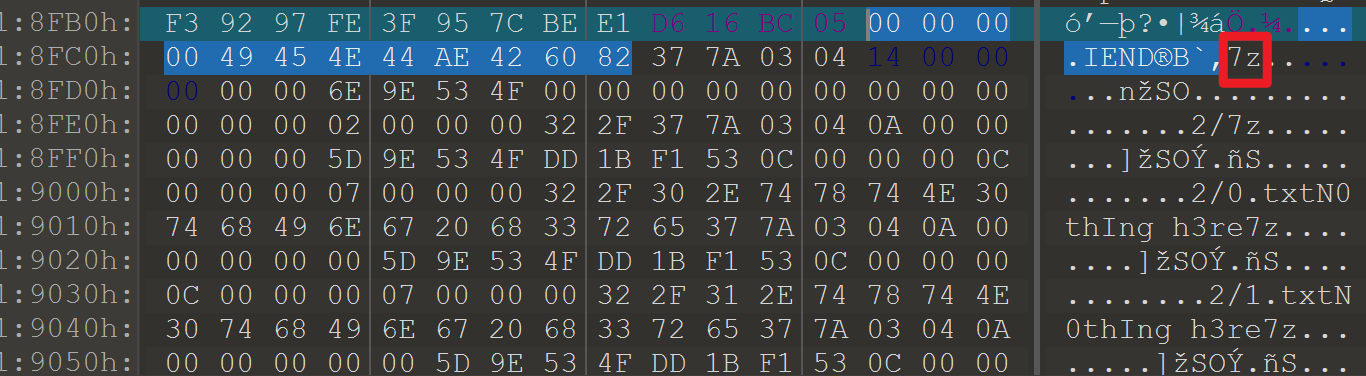
在2.png的文件尾发现7z的字样,提取出来,而后发现PK被修改成7z,解压得到1000个txt。
大小排序得到隐藏信息1RVcmVfc
3.png的每一个chunk的crc32都是一个字符的ascii编码,得到3RlZ30=
4.png和5.png直接用010查看即可
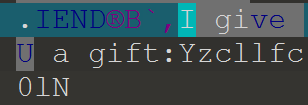
按照P1-P5-P4-P2-P3拼接得到ZmxhZ3s0X3Yzcllfc0lNcExlX1BsY1RVcmVfc3RlZ30=,解码得到flag。
0x03 我爱Linux
图片FFD9后存在冗余数据,导出另存为。
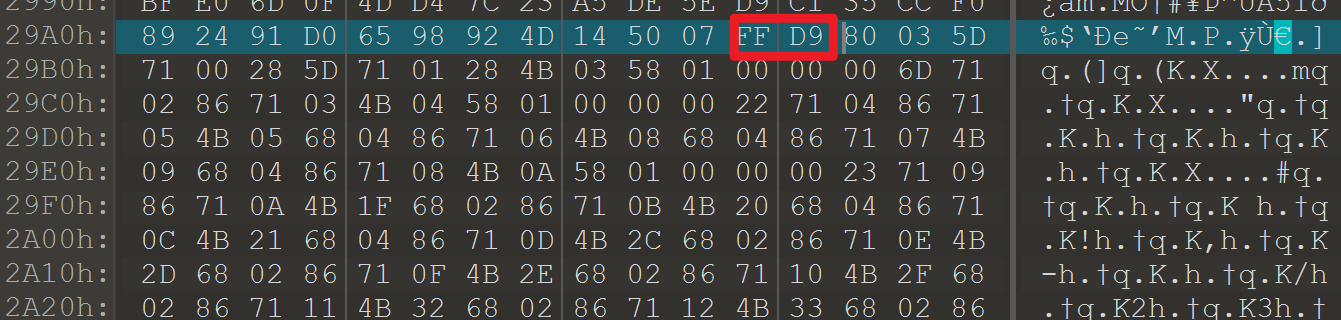
看了wp才知道得到的文件内容是Python Picke序列化内容,直接用脚本提取
import pickle
fp = open("123.txt","rb+")
fw = open('pickle.txt', 'w')
a=pickle.load(fp)
pickle=str(a)
fw.write( pickle )
fw.close()得到一系列坐标代码
|
|
再利用脚本进行转换
fw = open("pickle.txt","r")
text=fw.read( )
i=0
a=0
while i<len(text)+1:
if(text[i]==']'):
print('\n')
a=0
elif(text[i]=='('):
if(text[i+2]==','):
b=text[i+1]
d=text[i+1]
b=int(b)-int(a)
c=1
while c<b:
print(" ", end="")
c += 1
print(text[i+5], end="")
a=int(d)
else:
b=text[i+1]+text[i+2]
d=text[i+1]+text[i+2]
b=int(b)-int(a)
c=1
while c<b:
print(" ", end="")
c += 1
print(text[i+6], end="")
a=int(d)
i +=1解出来的字符可以看出是flag。
0x04 大流量分析(一)
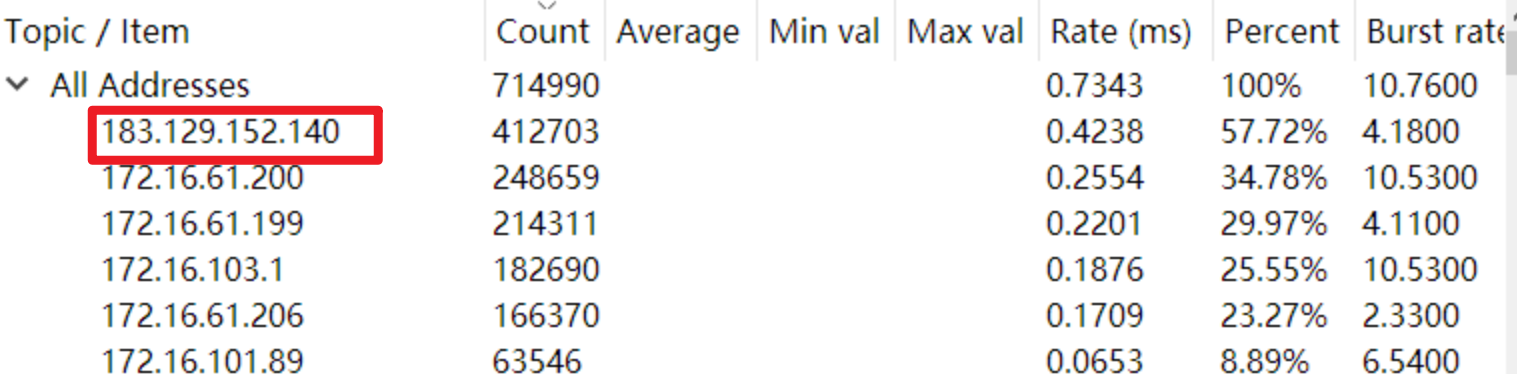
某黑客对A公司发动了攻击,以下是一段时间内我们获取到的流量包,那黑客的攻击ip是多少?
下载流量包后通过wireshark的统计功能,筛选出最多的ip,得到183.129.152.140。
0x05 大流量分析(二)
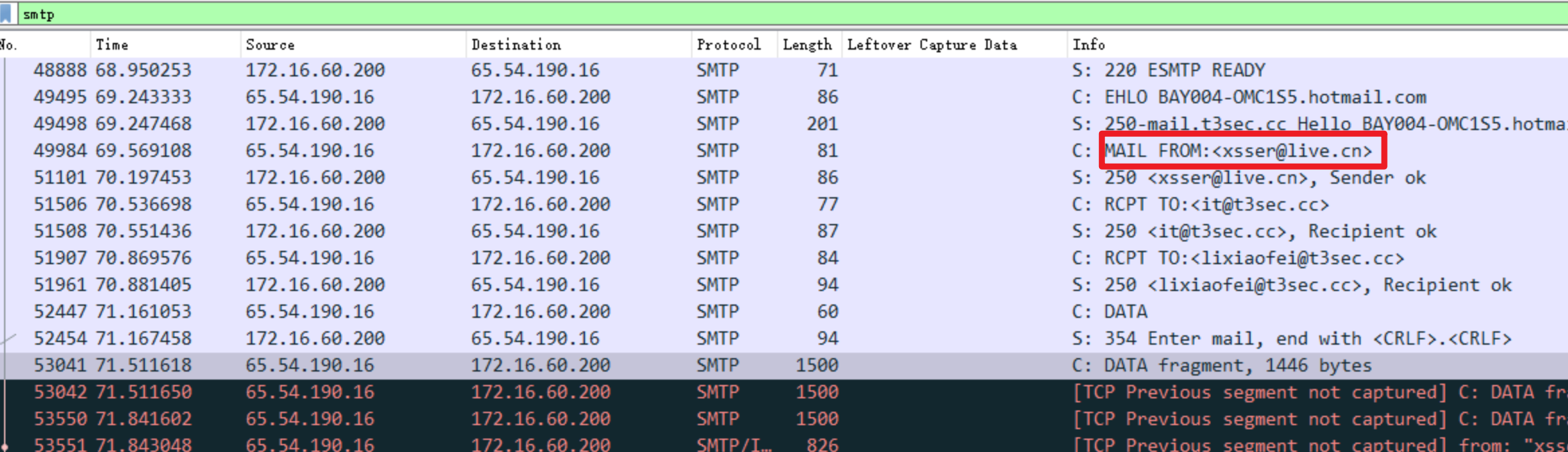
黑客对A公司发动了攻击,以下是一段时间内获取到的流量包,那黑客使用了哪个邮箱给员工发送了钓鱼邮件?
由于是邮件,所以首先过滤SMTP协议,然后一个个查看邮件的内容,最后确认邮箱为xsser@live.cn。
0x06 [NPUCTF2020]碰上彩虹,吃定彩虹!
在lookatme.txt中发现空白字符,转换得到.-/..-/-/---/-.-/./-.--,解密得到AUTOKEY,应该使用了AUTOKEY加密

使用https://github.com/Yoshino-s/breakautokey来进行爆破,得到iamthepassword
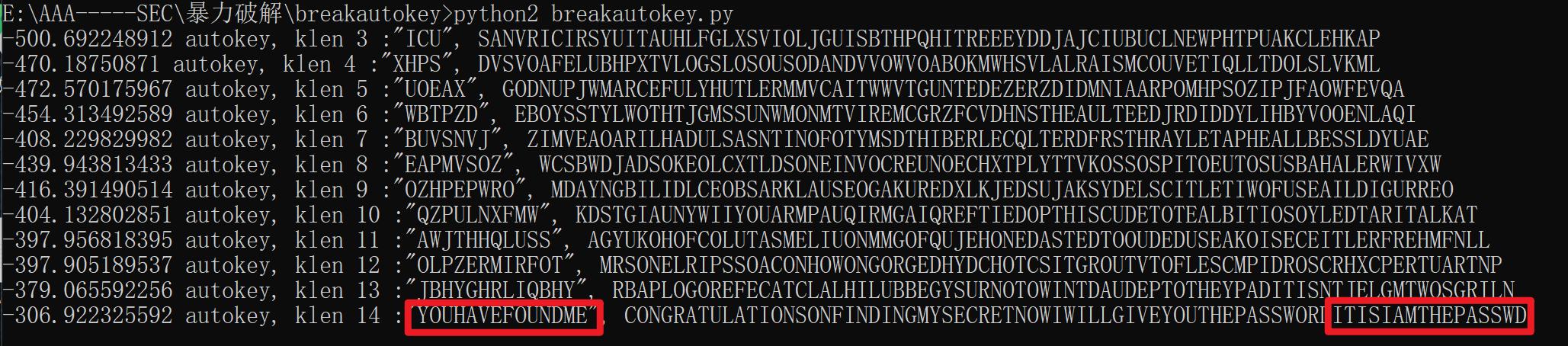
maybehint.txt 提示隐藏了一些信息,用 vim 查看
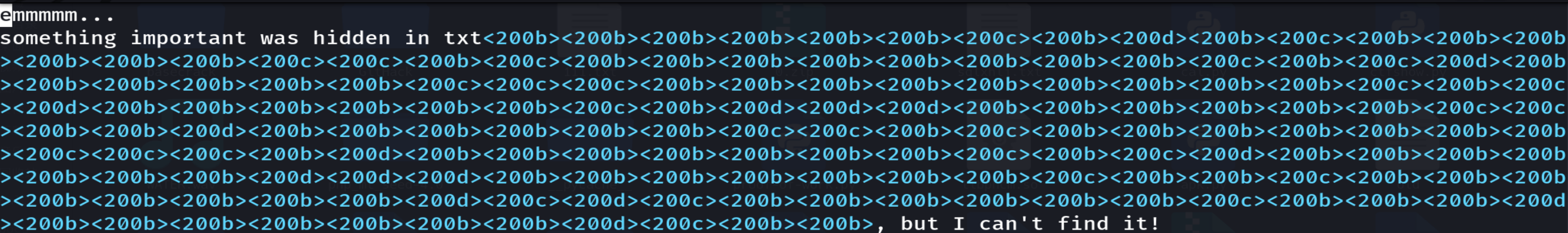
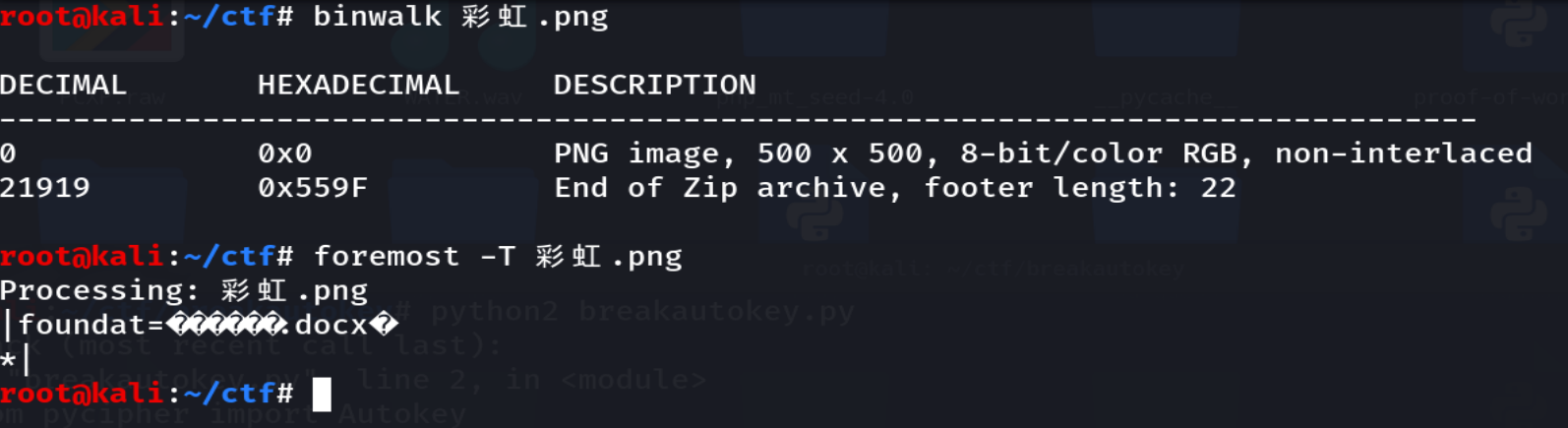
零宽字符隐写,在http://330k.github.io/misc_tools/unicode_steganography.html网站进行解密

使用ntfsstreamseditor 发现隐藏信息
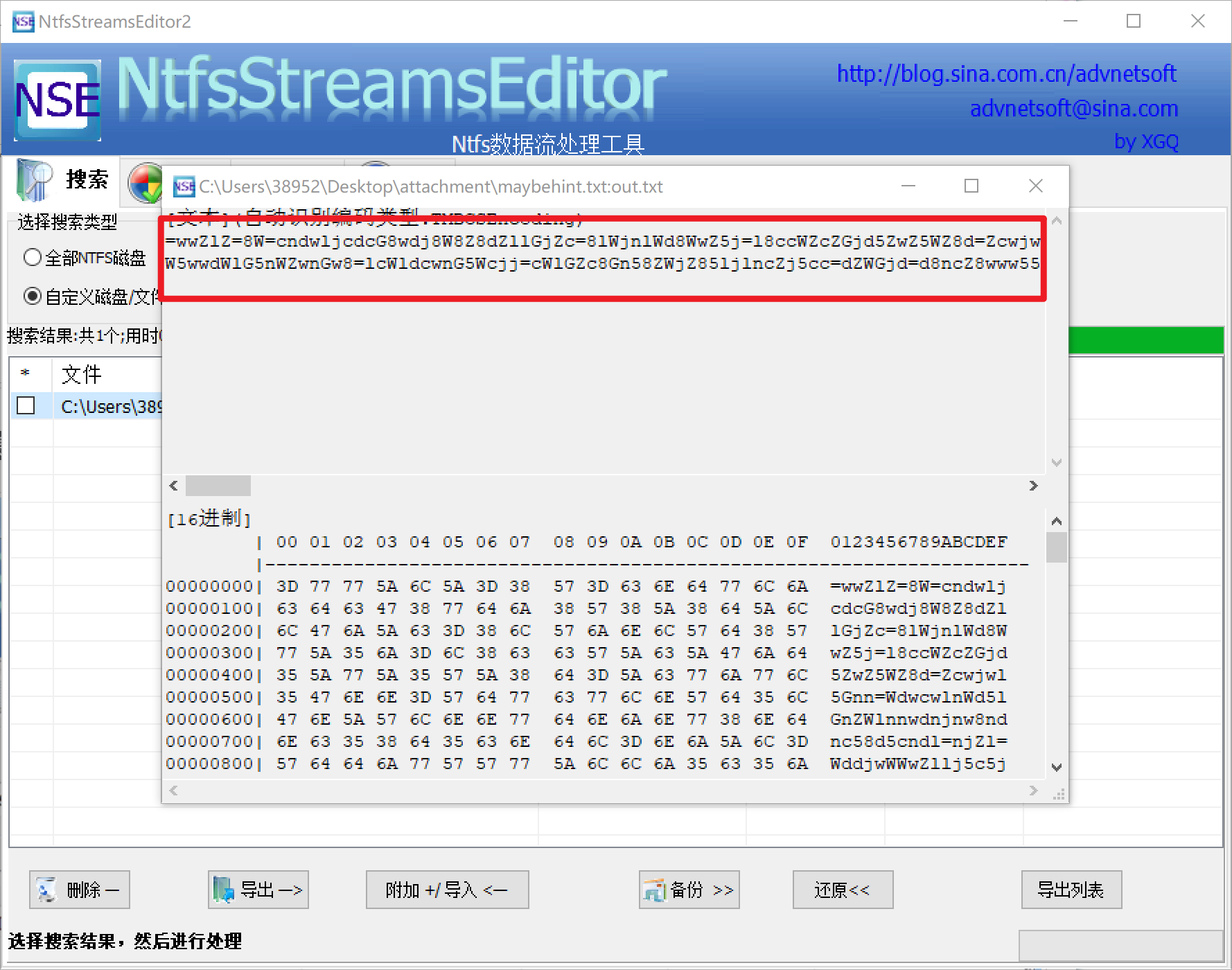
字符有限且不断循环,使用脚本计算词频,最后得到ZW5jcnlwdG8=,解base64得到encrypto
from collections import Counter
f=open('out.txt','r')
f_read=f.read()
print (Counter(f_read))
百度搜索发现这是一款软件,下载安装,其加密的文件后缀名为.crypto,打开得到hint,用autokey爆破得到的密码进行解压。

解压发现解不出,进一步分析发现。
得到一张彩虹.png
分析发现存在隐藏的zip,foremost提取出来。
得到的图片,用snipate对分段的黄色进行屏幕取色,得到
#ffff70
#ffff3f
#ffff73
#ffff73
#ffff57
#ffff64将后两位拼凑在一起,转ascii得到密码p@ssWd,解压得到内容
|
|
分析发现加密方式为Alphuck,进行转换即可得到flag。
0x07 [羊城杯 2020]signin
|
|
signin.txt里的内容如下
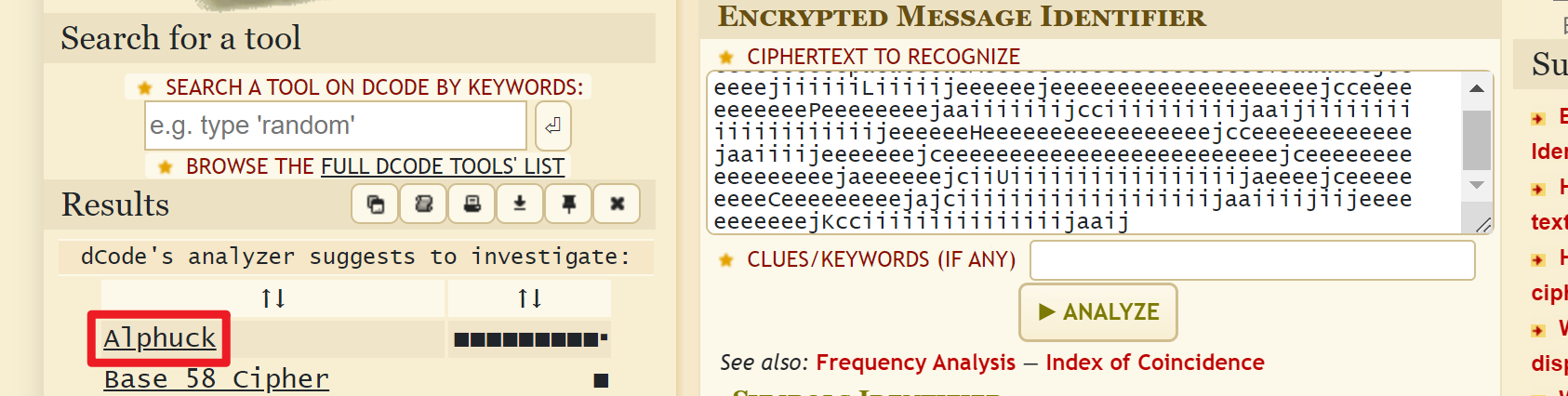
BCEHACEIBDEIBDEHBDEHADEIACEGACFIBDFHACEGBCEHBCFIBDEGBDEGADFGBDEHBDEGBDFHBCEGACFIBCFGADEIADEIADFH卡在这里很久,参考https://blog.csdn.net/mochu7777777/article/details/116056136才知道这个加密是Toy Cipher: https://eprint.iacr.org/2020/301.pdf
脚本如下:
|
|
0x08 [WMCTF2020]行为艺术
解压得到hint.txt
md5sum flag.zip
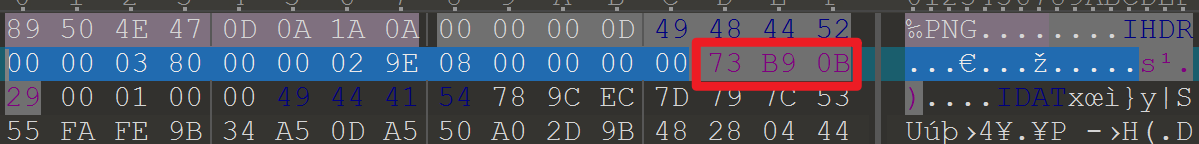
17f5b08342cf65f6dc08ed0b4c9bd334 flag.zip图片crc32存在问题,修改高度。
最后的图很像机器学习数据集,504b的开头联想到压缩包,参考https://hachp1.github.io/posts/%E6%9C%BA%E5%99%A8%E5%AD%A6%E4%B9%A0/20200814-wm2020.html#%E5%A6%82%E4%BD%95%E8%AF%86%E5%88%AB%E5%AD%97%E6%AF%8D

提取的数据为
|
|
转换成压缩包,解开伪加密,得到的文本转brainfuck即可得到flag。
Good eyes! Here is your flag:
https://www.splitbrain.org/services/ook
+++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++ [->-- -<]>- .<+++ [->-- -<]>-
.<+++ +[->+ +++<] >+.<+ ++[-> ---<] >---- -.<++ +++++ [->++ +++++ <]>++
++.-- --.<+ +++[- >---- <]>-- ----. +++++ +++.< +++[- >---< ]>-.+ ++.++
+++++ .<+++ [->-- -<]>- .+++. -.... --.++ +.<++ +[->+ ++<]> ++++. <++++
++++[ ->--- ----- <]>-- ----- ----- --.<+ +++[- >++++ <]>+. +...< +++++
+++[- >++++ ++++< ]>+++ +++++ +++.. .-.<